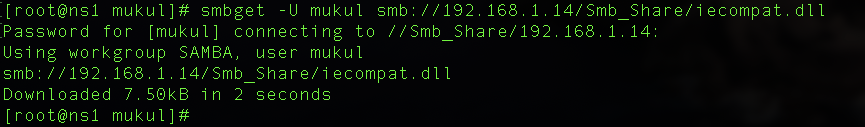
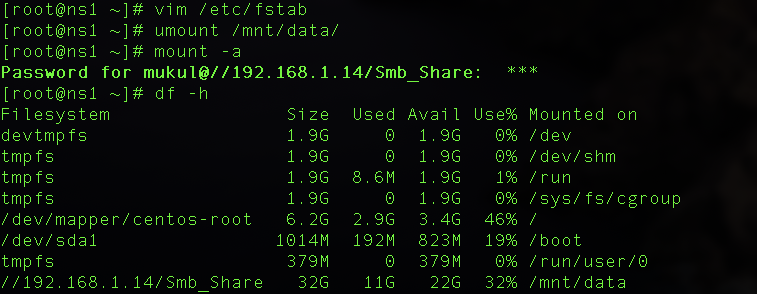
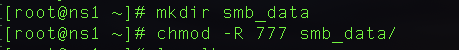
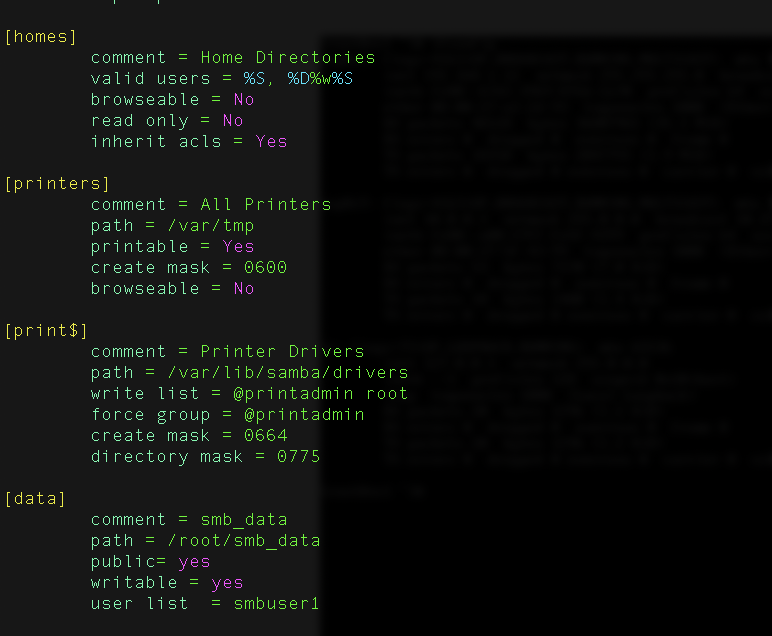
Before understanding run levels lets understand the booting stages first. The following are the 6 high-level stages of a Linux boot process.
1 BIOS: basic input/output system, Perform some system integrity checks and executes the boot loader program.
2 MBR: Master boot record, loads and executes the Grub boot loader.
3 GRUB: Grand Unified Boot-loader, it loads the default kernel image as specified in the grub configuration file.
4 Kernel: Kernel executes the /sbin/init program.
5 Init: init executes run levels program.
6. Run-level programs: A run levels is a state or level of init process means A run-level can simply be thought of as the state your system enters like if a system is in a single-user mode it will have a run-level 1 while if the system is in a multi-user mode it will have a run level 5.
Linux relies on the run level to determine which services are started and which services are stopped. Run levels are identified by numbers. Run levels are numbered from 0 to 6, with each run level offering different services. Run levels 0, 1, and 6 are standard run levels reserved for special purposes. Run levels 2, 3, and 4 are used for whatever purpose you or your Linux distribution provider decide.
Init scripts
Init (initialization) is the program on Unix and Unix-like systems that spawns all other processes. It runs as a daemon and typically has PID 1.
The /etc/inittab file is used to set the default run level for the system. This is the run level that a system will start up on upon reboot. The applications that are started by init are located in the /etc/rc.d folder. Within this directory, there is a separate folder for each run level, eg rc0.d, rc1.d, and so on.
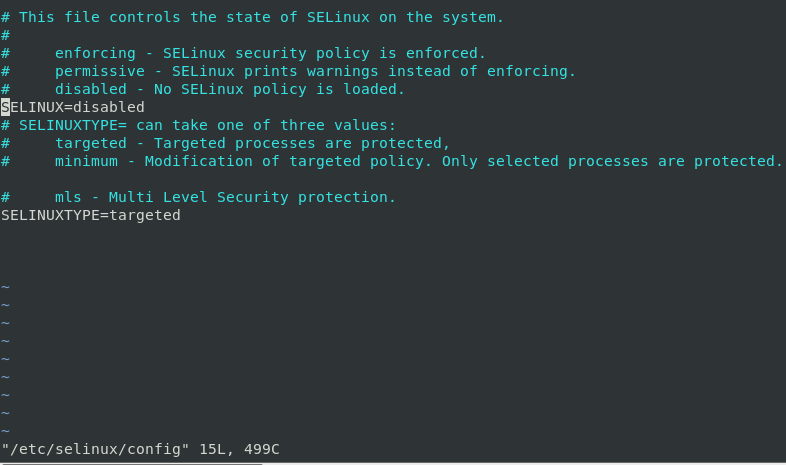
Example of /etc/inittab file:

Image via [https://geek-university.com/linux/runlevels/]
Depending on your default init level setting, the system will execute the programs from one of the following directories.
run levels 0 – /etc/rc.d/rc0.d/
run levels 1 – /etc/rc.d/rc1.d/
run levels 2 – /etc/rc.d/rc2.d/
run levels 3 – /etc/rc.d/rc3.d/
run levels 4 – /etc/rc.d/rc4.d/
run levels 5 – /etc/rc.d/rc5.d/
run levels 6 – /etc/rc.d/rc6.d/
Please note that there are also symbolic links available for these directory under /etc directly. So, /etc/rc0.d is linked to /etc/rc.d/rc0.d.
Under the /etc/rc.d/rc*.d/ directories, you would see programs that start with S and K.
Programs start with S are used during startup. S for startup.
Programs start with K are used during shutdown. K for kill.
When init starts, it looks for a line in /etc/inittab that specifies the default run level:
id : 2 : initdefault:
You can ask init to go to a non-default run level at startup by giving the kernel a command-line argument of single or emergency. Kernel command-line arguments can be given via LILO, for example. This allows you to choose the single user mode (run level 1).
While the system is running, the telinit command can change the run level. When the run level is changed, init runs the relevant command from /etc/inittab.
A system can be booted any of several run-levels, each of which is represented by a single-digit integer. Each run-levels designates a different system configuration and allows access to a different combination of processes.
There are differences in the run-levels according to the operating system. Seven run-levels are supported in the standard Linux Kernel. They are
ID | Name | Description |
0 | Halt | Shuts down the system. |
1 | Single-user mode | Mode for administrative tasks.[2][b] |
2 | Multi-user mode | It does not configure network interfaces and does not export network services.[c] |
3 | Multi-user mode with networking | Starts the system normally. |
4 | Not used/user-definable | For special purposes. |
5 | Start the system normally with appropriate display manager (with GUI) | Same as run-level 3 + display manager. |
6 | Reboot | Reboots the system. |
Image via[https://en.wikipedia.org/wiki/Runlevel]
In addition to the standard run levels, users can modify the preset run levels or even create new ones if desired. Run levels 2 and 4 are usually used for user-defined run levels.
The program responsible for altering the run level is init, and it can be called using the telinit command. For example, changing from run level 3 to run level 5, which allows the GUI to be started, can be accomplished by the root (i.e., administrative) user by issuing the following command: telinit 5
Booting into a different run level can help solve certain problems. For example, if a change made in the X Windows System configuration on a machine that has been set up to boot into a GUI has rendered the system unusable, it is possible to temporarily boot into a console (i.e., all-text mode) run level (i.e., run levels 3 or 1) to repair the error and then reboot into the GUI. The X Window System is a widely used system for managing GUIs on a single computer and on the network of computers.
Likewise, if a machine will not boot due to a damaged configuration file or will not allow logging in because of a corrupted /etc/passwd file (which stores user names and other data about users) or because of a forgotten password, the problem can be solved by first booting into single-user mode (i.e. run level 1).
The chkconfig tool is used in Red Hat-based systems (like CentOS) to control what services are started at which run levels. Running the command chkconfig - - list will display a list of services whether they are enabled or disabled for each run level.
In recent versions of Linux systems such as RHEL 7, the concept of run levels has been replaced with systemd targets.
Systemd
Inittab is no longer used when using systemd
Systemd- system daemon is a new system that replaces the old “system V init” which gives all booting privileges to init generated process.systemd is developed and designed for better handling of dependencies and multitasking.
Systemd uses target instead of run levels, which supports our machine to keep track of all processes especially the daemon process(background running processes). The main purpose for develop this target based system is to perform parallel processing. All the new and popular Linux distribution such as Centos 7, RHEL 7.0, Fedora, and Arch Linux uses this
Runlevel | Systemd Description |
0 | poweroff.target |
1 | rescue.target |
2 | multi-user.target |
3 | multi-user.target |
4 | multi-user.target |
5 | graphical.target |
6 | reboot.target |
By default, there are 2 main targets
- Multi-user.taget: Analogous to Runlevel 3
- Graphical.target: Analogous to run level 5
To view current default target run: systemctl -getdefault

And to change the default target: rm /etc/systemd/system/default.target
Changing run level to 5:
ln -s /lib/systemd/system/runlevel5.target /etc/systemd/system/default.target
Then reboot system to use runlevel5